CipherTrust Transparent Encryption for Kubernetes enables protection of sensitive data on persistent volumes via encryption, user and process-based access controls, and data access logging. This solution enables developers to establish security controls inside of containers. With this extension for CipherTrust Transparent Encryption, data protection can be applied on a per-container basis, both to data inside of containers and to external storage accessible from containers.
COMPLIANCE
CipherTrust Transparent Encryption for Kubernetes addresses compliance requirements and regulatory mandates for protecting sensitive data and sensitive assets.
PROTECTION FROM PRIVILEGED-USER THREATS
The solution offers encryption with data access control. This lets privileged users, such as Kubernetes cluster administrators, operate as regular users without gaining unauthorized access to sensitive data.
ACHIEVE ROBUST SECURITY
CipherTrust Transparent Encryption for Kubernetes enforces data security policies wherever the data is stored or used, including data centers, virtualized environments, and even in cloud implementations. Your organization can securely deploy and use Kubernetes applications where needed for cost effectiveness, control, or performance without having to make any changes to applications, containers, or infrastructure sets.
COMPREHENSIVE DATA SECURITY SAFEGUARDS
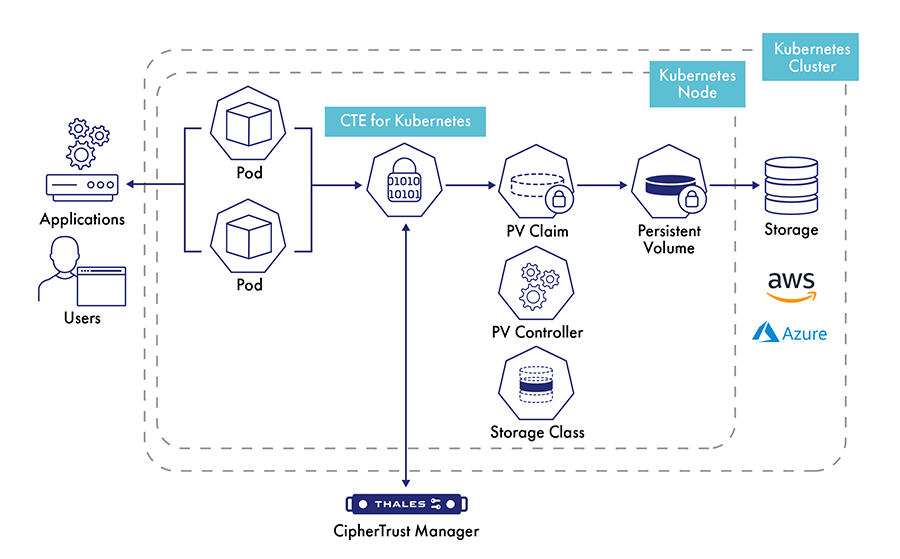
CipherTrust Transparent Encryption for Kubernetes extends CipherTrust Transparent Encryption, so security teams can establish data security controls inside of containers. Enterprises can apply encryption, access control, and data access logging on a per-container basis. Encryption is applied to persistent volumes attached to containerized applications with the ability to restrict data access to approved set of users and processes.
TRANSPARENT ENCRYPTION
Transparent encryption lets users establish data security controls without having to make any changes to applications, containers, or infrastructure sets. The solution supports common container micro-services deployment models. This enables deploying same protection policies for all persistent volumes attached to an application pod or have unique encryption and access control for each persistent volume in a Kubernetes Cluster.
GRANULAR ACCESS CONTROLS AND VISIBILITY
CipherTrust Transparent Encryption for Kubernetes offers the detailed visibility and control you need to comply with the most stringent regulations, policies, and mandates. Enterprises can establish granular access policies based on specific users, processes, and resource sets within containers. In addition, this solution can establish isolation between containers, so only authorized containers can access sensitive information.
