It is costly and complex for IT organizations to protect data using multiple encryption technologies across disparate data silos, such as file-servers, databases, virtual environments, and cloud storage.
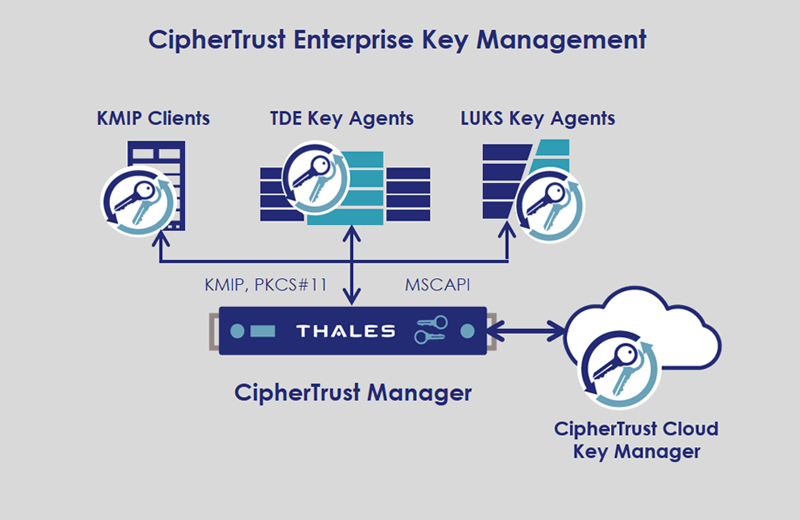
Enterprise Key Management solutions from Thales TCT, enable organizations to centrally manage and store cryptographic keys and policies for third-party devices including a variety of KMIP Clients, TDE Agents on Oracle and Microsoft SQL Servers, and Linux Unified Key Setup (LUKS) Agents on Linux Servers. CipherTrust Enterprise Key Management delivers a robust, standards-based platform for managing encryption keys to protect data in disparate storage repositories across the enterprise. It simplifies the administrative challenges around encryption key management to ensure that keys are secure and always provisioned to authorized encryption services.
Unify Key and Certificate Management
Leverage CipherTrust Manager for managing keys for Thales data protection connectors and third-party applications including Microsoft SQL TDE, Oracle TDE, and KMIP-compliant encryption products.
Improve Operational Efficiency
Enterprise Key Management simplifies the process of managing cryptographic keys, enabling security teams to gradually consolidate the management of encryption across the enterprise that can reduce cost of ownership and minimize overall risks.
Prevent Unplanned Downtime
Minimize key availability and redundancy, leveraging secure replication of keys across multiple appliances with automated backups. Automated alerts help prevent unexpected key expiration.
CipherTrust Manager offers the following Enterprise Key Management solutions.
CipherTrust KMIP Clients:
Centrally manage keys across a variety of KMIP clients.
CipherTrust TDE Key Agents:
Protects data in databases using Transparent Data Encryption (TDE) Key Agents on Oracle and Microsoft SQL Servers.
CipherTrust LUKS Agents:
provides transparent data encryption on Linux servers using Linux Unified Key Setup (LUKS) Agents.
CipherTrust Cloud Key Manager:
Supports BYOK use-cases by centrally managing keys for multi-cloud environments, such as AWS, Microsoft Azure, Salesforce and more.
Secrets Management
- Opaque Objects, Passwords, X.509 certificates
- Symmetric and asymmetric encryption keys
Administration
- Secure-web (CipherTrust Platform management console), CLI, REST API
- Bulk import of digital certificates and encryption keys
- Command line scripts
Key and Certificate Formats for Search, Alerts, and Reports
- Symmetric encryption key algorithms: AES (default=128, 192, 256), ARIA), ARIA (default=128, 192, 256)
- Asymmetric encryption key algorithms: RSA (512, default=1024, 2048, 3072, 4096)
- Digital certificates (X.509): DER, PEM, PKCS#7, PKCS#8, PKCS#12
Third-Party Encryption
- Microsoft SQL TDE, Oracle TDE, IBM Security Guardium Data Encryption, KMIP-clients
- Partner Categories: Tape Libraries, Enterprise Storage, Efficient Storage, Enterprise Servers, Database Servers, Virtual Environments, Cloud/SaaS, Backup & Recovery
API Support
- RESTful, Microsoft Crypto API (MS-CAPI), PKCS#11, OASIS KMIP
Key Availability and Redundancy
- Secure replication of keys across multiple appliances with automated backups
| Image | Title | Link |
|---|---|---|
| CipherTrust Encryption key management solutions for Microsoft® SQL Server® and Oracle® Database Solution Brief | ||
| CipherTrust Manager k160 Product Brief | ||
| CipherTrust Manager k570 Product Brief | ||
| CipherTrust Manager Product Brief | ||
| DoD STIG Compliance Virtualization-Based Security – External Key Management Solution Brief | ||
| Enterprise Key Management for NetApp Solution Brief | ||
| Enterprise Key Management Solutions for KMIP Clients, TDE and LUKS Solution Brief | ||
| HPE 3PAR StoreServ and Thales CipherTrust Manager | ||
| HPE servers and storage with Thales CipherTrust Data Security Platform Solution Brief | ||
| Introduction to Thales’ CipherTrust Enterprise Key Management Solutions | ||
| NetApp and Thales TCT Solution Brief | ||
| Nutanix and Thales TCT Solution Brief | ||
| Virtual CipherTrust Manager Product Brief | ||
| White Paper: Best Practices for Cloud Data Protection and Key Management | ||
| White Paper: Best Practices for Cryptographic Key Management | ||
| White Paper: Key Management | ||
| White Paper: Own and Manage Your Encryption Keys | ||
| White Paper: The Importance of KMIP Standard for Centralized Key Management |






