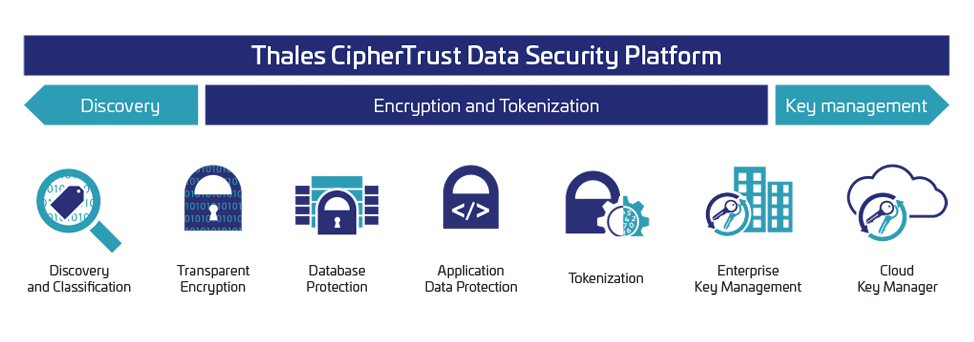
Whether storing data-at-rest in a physical data center, a private or public cloud, or in a third-party storage application, proper encryption and key management are critical factors in ensuring sensitive data is protected.
Thales TCT offers federal agencies data encryption solutions that deliver granular encryption and role-based access control for structured and unstructured data residing in databases, applications, files, and storage containers. With centralized key management and a hardened root of trust, agencies can ensure their master keys are protected and data remains secure.
Simplicity
Centralized policy and encryption key management to assure control of your data across every physical and virtual server on and off your premises.
Minimize Risk
Meet compliance and best practice requirements for protecting data from external threats or malicious insiders with proven, high-performance and scalable data encryption.
Security Agility
Quickly address new data security requirements and compliance mandates by having an encryption solution in place ready and able to encrypt everything.
Database Security
Encrypt data, control privileged user access, and collect security intelligence logs across your heterogeneous collection of database and big data environments with TCT data encryption security solutions.
Compliance
Data encryption, user and process access controls, logs, FIPS 140-2 and Common Criteria compliant key management, strong administration policies all contribute to effectively satisfying compliance mandates and regulation requirements.
Cloud Security
Confidently move workloads to the cloud and hosted environments knowing that your data remains in your control through data encryption and key management.
