 EMAIL: THE MOST POPULAR TARGET FOR MALICIOUS ATTACKS
EMAIL: THE MOST POPULAR TARGET FOR MALICIOUS ATTACKS
Email is so essential to work, most employees use it without thinking. Hackers easily exploit this by targeting individuals in organizations with weaponized files they least suspect. And because current solutions aren’t designed to catch every threat, businesses are always one click away from disaster.
Votiro Secure File Gateway for Email is available for sale to the U.S. Federal Government exclusively through Thales Trusted Cyber Technologies.
SECURE 100% OF EMAILS WITH POSITIVE SELECTION TECHNOLOGY™
Secure File Gateway for email singles out only the elements of emails known to be fully secure, guaranteeing they are 100% safe. Now employees can open every email and file attachment with complete peace of mind, and without any delays or disruptions to business.
Built with deep expertise in the architecture of every file format, Votiro’s Secure File Gateway understands and protects all file types—from .ppt, docs, pdfs and image files, all the way to more complex formats like Autodesk files. Powered by Positive Selection technology, Votiro’s Secure File Gateway protects from even the most obscure, challenging file types that no NGAV or Sandbox can possibly detect.

Defend all emails & attachments

Protect every email
without blocking access

Be more productive
with zero interruptions
Protects the entire email channel from malicious threats, ensuring your email is 100% safe.
See the emails you need right away, without waiting for IT middle-men to unblock access.
Runs invisibly in the background, with virtually no latency.
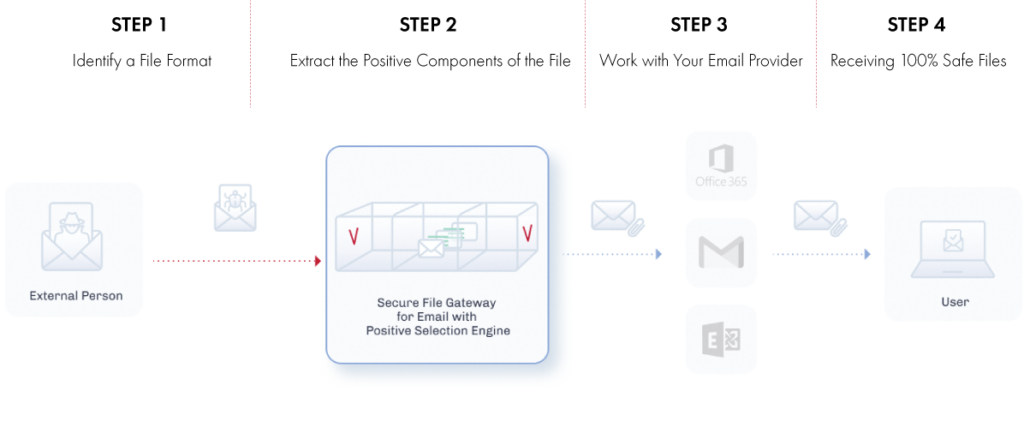
Phase 1: Identify the File Format
Every file must adhere to strict, vendor-based specifications that are unique to that particular file format. Positive Selection technology uses an intelligent fingerprinting technique that identifies a file’s content type and format based on file structure and characteristics.
Phase 2: Generate a New Version of the File
Positive Selection technology then generates a new, clean template of the file and imports over the content from the original file while leaving behind exploits and malicious objects. This regenerated, safe version of the file, based on known good templates from the file vendors, ensures that all the content (including active content and embedded objects) is kept in its original format while preserving file functionality.
Macros, scripts, OLE objects, and all other elements are sanitized and regenerated into the new file as usable elements, neutralizing any exploitation attempts. This process ensures that both the user experience and file security remain intact. All files—suspicious or not—go through this process, which takes less than a second and is invisible from the user’s point of view.
Phase 3: Use the New File
All malicious code and exploit threats are sanitized, and the new file preserves the integrity and functionality of the original file. The file is now safe to save, edit, use, and share.
- Easy Implementation in less Than 10 Minutes
- Seamless Integration With Existing Solutions
- Zero training required
- Supports Both Cloud & On-Prem
| Image | Title | Link |
|---|---|---|
| CTO Sessions On Demand: Preventing Ransomware in Microsoft 365 Environments | ||
| CTO Sessions Webcast On Demand: AI & Cybersecurity | ||
| eBook: Ryuk: Everything You Need to Know About the Ransomware Targeting U.S. Governments & Government Agencies | ||
| On Demand Webinar: No-Excuse Defenses Against Supply Chain Attacks | ||
| Votiro + Office 365 Solution Brief | ||
| Votiro Secure File Gateway for Email | ||
| Votiro Secure File Gateway for Web Applications | ||
| Votiro Secure File Gateway vs Secure Email Gateway Solution Brief | ||
| White Paper: Malicious Macros |





