True data protection extends to edge. Agencies need to apply the same level of security deployed in the core and the cloud to edge environments.
Thales Trusted Cyber Technologies (TCT), a US-based provider of cybersecurity solutions, offers unified data protection solutions that reduce the risks associated with the most critical attack vectors at the edge and solve for the government’s most stringent encryption, key management, and access control requirements. Our solutions easily integrate into an existing cybersecurity infrastructure to extend your agency’s data protection ecosystem to the edge. Whether integrated with a third-party product or used as standalone solution, we can tackle a wide range of mission-critical challenges. Our solutions can be cost-effectively deployed across enclave environments or scale to large number of disconnected environments.
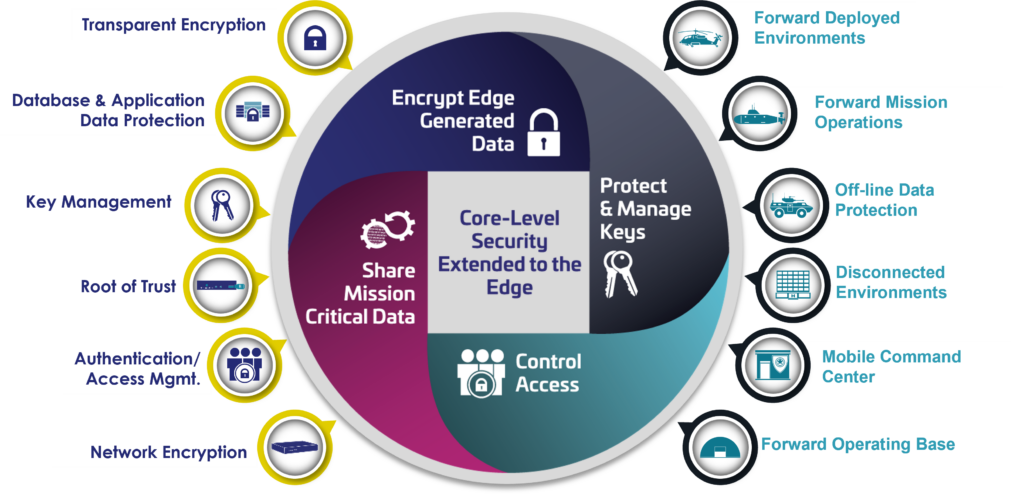


 PCentralize and simplify data security policies and key management at the edge.
PCentralize and simplify data security policies and key management at the edge. Secure access to resources and data while protecting user identities.
Secure access to resources and data while protecting user identities. Protect mission-critical data in transit from the core to the cloud to the edge.
Protect mission-critical data in transit from the core to the cloud to the edge.
