Despite large scale quantum computing being several years away from being a practical reality, federal government experts are deservedly concerned about the cybersecurity implications today. Federal agencies need to start their quantum safe transition strategy now.
This was underscored in May 2022, when the National Security Memorandum on Promoting United States Leadership in Quantum Computing While Mitigating Risks to Vulnerable Cryptographic Systems (NSM 10) provided requirements and timelines for Quantum-Resistant Cryptography. In particular, the memo notes that “America must start the lengthy process of updating our IT infrastructure today to protect against this quantum computing threat tomorrow.”
The memo continues by underscoring that, “Central to this migration effort will be an emphasis on cryptographic agility, both to reduce the time required to transition and to allow for seamless updates for future cryptographic standards.”
Today’s non-PQ (post-quantum) encryption absolutely will break (or be broken) in the future, affecting security aspects such as authentication, code-signing, and digital signatures.
Understanding Post-Quantum Cryptography (PQC)
Post-Quantum Readiness Starts with Crypto-Agility
Crypto-agility is a strategy that enables you to future-proof your organization by:
- Having the flexibility to quickly change protocols, keys, and algorithms
- Using flexible, upgradeable technology
- Reacting quickly to cryptographic threats, such as Quantum computing
- Adding to your tech stack with minimal to no disruption
Thales TCT’s products have been purposely designed to help you be crypto-agile and quantum-safe.
Strategy for Migration to Post-Quantum Crypto
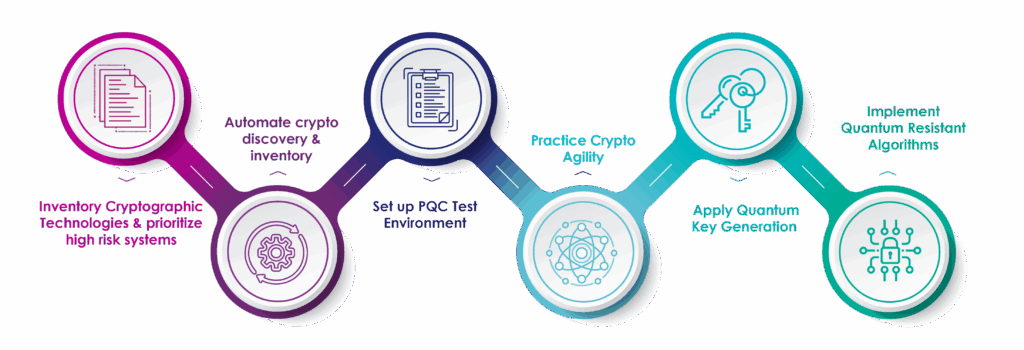
Inventory cryptographic technologies and prioritize high-risk systems. Although the May 4, 2023 deadline for agencies to submit a list of their prioritized crypto inventory has passed, it’s critical for agencies continue this process to ensure that newly deployed systems are on track to be quantum safe.
Automate crypto discovery. Since the crypto inventory process is continuous, automating crypto discovery (versus using a manual process) is the most effective way of keeping track of new or updated crypto systems. There are many solutions available for the automation of crypto discovery and inventory. With automated tools, agencies will have accurate inventory of their crypto .
Set up a PQC test environment. Many encryption vendors have already implemented pre-PQC standard algorithms in their solutions. With NIST’s release of the PQC standards in August 2024, there should no longer be a delay in upgrading your agency’s environment. The PQC algorithms’ impact needs to be tested—the standardized algorithms will generate larger keys, and the size of those larger keys could affect overall performance.
Practice crypto agility. Crypto-agile solutions support both classic algorithms and PQC algorithms. When deploying crypto today, agencies should ensure that their solutions are crypto-agile to prepare for the future.
Apply quantum key generation The quality of the cryptographic keys used to encrypt and decrypt data is the foundation of encryption. If these keys are compromised, data is at risk. Agencies should leverage a quantum random number generator to generate quantum-enhanced keys. QRNGs produce high quality entropy which is the basis for all random numbers and cryptographic keys.
Implement quantum resistant algorithms. Agencies need to ensure that their encryption solutions are using the standardized PQC algorithms—or are crypto-agile and have an upgrade path to utilize PCQ algorithms in the near future.
Securing the Future: Navigation Post Quantum Cryptography Standards
Thales TCT joins NG/FCW and government leaders to share actionable strategies and resources for navigating this evolving landscape, empowering organizations to safeguard against emerging cyber risks. This discussion will explore the latest initiatives, offering practical insights on implementing PQC standards to protect sensitive data.
Thales TCT Quantum-Ready Solutions
Thales TCT has integrated PQC into its high-assurance cryptographic solutions and incorporate crypto-agile frameworks to adapt to evolving PQC requirements. By aligning with NIST-standardized PQC algorithms, leveraging crypto-agility, and collaborating with NIST and NSA, through a Cooperative Research and Development Agreement (CRADA), Thales TCT ensures quantum-resistant security for U.S. Government intelligence, defense, and civilian agencies.

Luna T-Series HSMs are the choice for government agencies when storing, protecting and managing cryptographic keys used to secure sensitive data and critical applications. Meeting government mandates for U.S. Supply Chain, the high-assurance, crypto-agile, tamper-resistant Luna T-Series HSMs are designed, developed, manufactured, sold, and supported in the United States.
Protect Encryption Keys with T-Series Luna Hardware Security Modules
Quantum Resistant Algorithms
Luna T-Series HSMs (v 7.13.0 forward) now include pre-standards implementations of NIST-selected PQC algorithms and stateful hashed-based signature algorithms.
The algorithms supported are:
- CRYSTALS-Dilithium (ML-DSA)
- CRYSTALS-KYBER (ML-KEM)
- FALCON (FN-DSA)
Additionally, Thales TCT is introducing the Leighton-Micali Signature (LMS) stateful hash-based signature mechanism, along with its multi-tree variant, the Hierarchical Signature Scheme (HSS). LMS/HSS enables customers to transition to quantum-resistant firmware/software signing. The Luna T-Series HSM implementation of LMS is compliant with SP 800-208 and PKCS#11 v3.1.
Quantum Enhanced Keys
By embedding a quantum random number generator (QRNG) chip within the Luna HSM, Thales TCT is offering the industry’s first FIPS 140-2 compliant HSM capable of generating quantum enhanced keys. Using principles of quantum physics, the QRNG chip produces high quality entropy which is the basis for all random numbers and cryptographic keys generated by the HSM. With a choice of operating the HSM in FIPS-approved mode using either the embedded, classic physical RNG or the embedded quantum RNG, customers can dynamically change between classical key generation and quantum enhanced keys as threats emerge over time.
Quantum Random Number Generation
QRNG complements post quantum cryptography and is part of a crypto-agile strategy. Thales TCT’s Luna T-Series HSMs contain an embedded QRNG chip for high quality entropy based on quantum noise.
All keys and random numbers generated within the HSM are enhanced by the security of the quantum random numbers that are the foundation of the key generation process.
Secure Data in Transit with High Speed Encryptors (HSE)
Quantum Resistant Algorithms
Thales HSEs include a framework to support QRA via firmware upgrade. Thales HSE solutions support all four NIST Quantum Resistant Public Key algorithms (finalists) in all products (plus other non-finalist algorithms).
Quantum Key Distribution
Thales HSEs are quantum-ready and QKD compatible for more than a decade.
Quantum Random Number Generation
Quantum Random Number Generation is integrated into the HSE solution.

Thales HSE network encryption solutions support Post-Quantum Cryptography with a crypto-agile, FPGA-based architecture.
Featured Resources
Resources
| Image | Title | Link |
|---|---|---|
| CTO Sessions On Demand: Trusted Data in Motion – Securing Government Communications in the PQC Era | ||
| On Demand Webinar: Get Started with Post-Quantum PKI: A Tech Spotlight from Thales TCT & Keyfactor | ||
| Tech Spotlight: Keyfactor and Thales Deliver Post-Quantum PKI for Federal Agencies | ||
| CTO Sessions On Demand: When AI Learns to Breach and Quantum Learns to Decrypt – The Endgame | ||
| Washington Technology Commentary: Why federal agencies must act now on post-quantum cryptography | ||
| CTO Sessions Webcast On Demand: Intersection of Quantum, AI and Security | ||
| Solution Brief: Thales TCT Post-Quantum Cryptography Implementation | ||
| Washington Technology Commentary: Why post-quantum security planning must start today | ||
| GovLoop Blog Post: Quantum-Safe Encryption: What It Means, and Why Agencies Should Care | ||
| On Demand GovLoop Webinar: Taking a Realistic Look at Quantum Computing in Government | ||
| GovLoop Video: Quantum-Safe Encryption: Understanding the What, Why and How | ||
| Govloop Video Interview: Quantum-Safe Encryption: What It Means, and Why Agencies Should Care | ||
| CTO Sessions On Demand: Best Practices for Implementing Quantum-Resistant Security | ||
| Securing the Future: Navigation Post Quantum Cryptography Standards | ||
| FedNewsNetwork Video Interview: Preparing for the intersection of AI, quantum computing | ||
| FedNewsNetwork Commentary: Preparing for the intersection of AI, quantum computing | ||
| Blog Post: PQC Standards Released – Start Today | ||
| CTO Sessions: Quantum Resistant Security | ||
| The Dual Faces of Quantum Computing: Opportunities and Threats in National Security | ||
| CTO Sessions Webcast: Word on the Street – 2024’s Top Tech Trends | ||
| White Paper: Quantum Resistant Code Signing Secured by Hardware Security Modules | ||
| CTO Sessions On Demand: Are You Quantum Ready? | ||
| Quantum Enhanced Keys Solution Brief |