Amazon Web Services (AWS) offers convenience and cost savings. However, you still need to follow security, privacy and compliance rules, as well as best practices, for protecting data. Further, you need rapid data mobility across all clouds you currently use and those in your future, a need which can be compromised with cloud-vendor-specific encryption solutions.
ADVANCED DATA PROTECTION FOR AWS
Effective, secure cloud use involves an increasing number of decisive moments, such as when you consider using sensitive data in any cloud. You can rely on Thales Trusted Cyber Technologies (TCT) to secure your digital transformation. Thales TCT’s advanced encryption and centralized key management solutions give you protection and control of data stored on your premises, Amazon Web Services, and other cloud providers. Thales TCT technology enables:
- Avoid cloud vendor encryption lock-in and ensure the data mobility you need while you efficiently and securely spread workloads and data across multiple cloud vendors, including AWS, with centralized, independent encryption management
- Take secure advantage of Amazon Key Management Services (AWS KMS) with a centralized key management solution that spans multiple clouds
- Identify attacks faster with data access logging to industry-leading SIEM applications
- Reduce or eliminate risks arising from compromised credentials with advanced encryption including privileged user access controls
- Architect applications for the cloud with built-in security using Vaultless Tokenization with Dynamic Data Masking
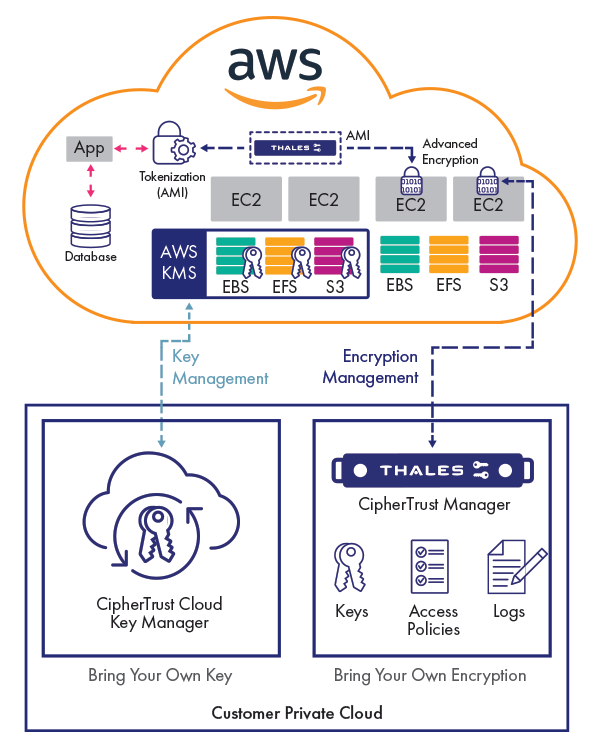
Bring Your Own Advanced Encryption to Amazon Web Services
If you’re 100% Amazon Web Services-based with stringent data security controls, or if you’re running hybrid clouds with data distributed across your on-premises private cloud, multiple cloud providers, and on AWS, you need an advanced data encryption solution. CipherTrust Transparent Encryption AWS data security protects your files and databases on your premises and across multiple clouds including AWS, without any changes to applications, databases, infrastructure or business practices.
AWS Encryption Key Management
Organizations that cannot bring their own encryption can still follow industry best practices by managing keys externally using the CipherTrust Cloud Key Management, which leverages cloud provider Bring Your Own Key API’s to reduce both key management complexity and reduce operational costs.
Centralized, secure key management
The CipherTrust Manager centralizes key, policy and log management for CipherTrust Transparent Encryption, available as a FIPS 140-2 Level 2 or 3 appliance or a FIPS 140-2 Level 1 AMI for AWS.
Resources
| Image | Title | Link |
|---|---|---|
| Advanced data protection for AWS S3 with CipherTrust Transparent Encryption Solution Brief | ||
| Avoiding Amazon S3 Data Leaks with Scalable Encryption and Access Controls Solution Brief | ||
| CipherTrust Cloud Key Management Solutions for Amazon Web Services Solution Brief | ||
| CTO Sessions On Demand: Protecting Your Data in Their Cloud | ||
| CTO Sessions Webcast: A Guide to BYOK and HYOK for AWS, Azure, Google, Oracle and More | ||
| Product Demo: Protecting AWS S3 Buckets: AWS KMS vs Transparent Encryption COS S3 from Thales | ||
| White Paper: Best Practices for Cloud Data Protection and Key Management | ||
| White Paper: Best Practices for Secure Cloud Migration | ||
| White Paper: The Case for Centralized Multicloud Encryption Key Management |







