Thales has pushed the innovation envelope with the CipherTrust Data Security Platform to remove complexity from data security, accelerate time to compliance, and secure cloud migrations. This next-generation platform is built on a modern micro-services architecture, is designed for the cloud, includes Data Discovery and Classification, and fuses together the best capabilities from the Vormetric Data Security Platform and KeySecure and connector products. CipherTrust Data Security Platform unifies data discovery, classification, data protection, and unprecedented granular access controls with centralized key management – all on a single platform. This results in less resources dedicated to data security operations, ubiquitous compliance controls, and significantly reduced risk across your agency.
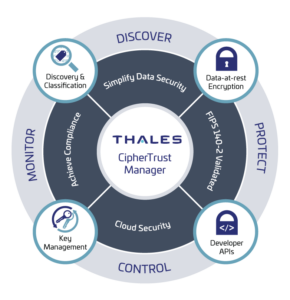
The CipherTrust Data Security Platform is an integrated suite of data-centric security products and solutions that unify data discovery, protection and control in one platform.
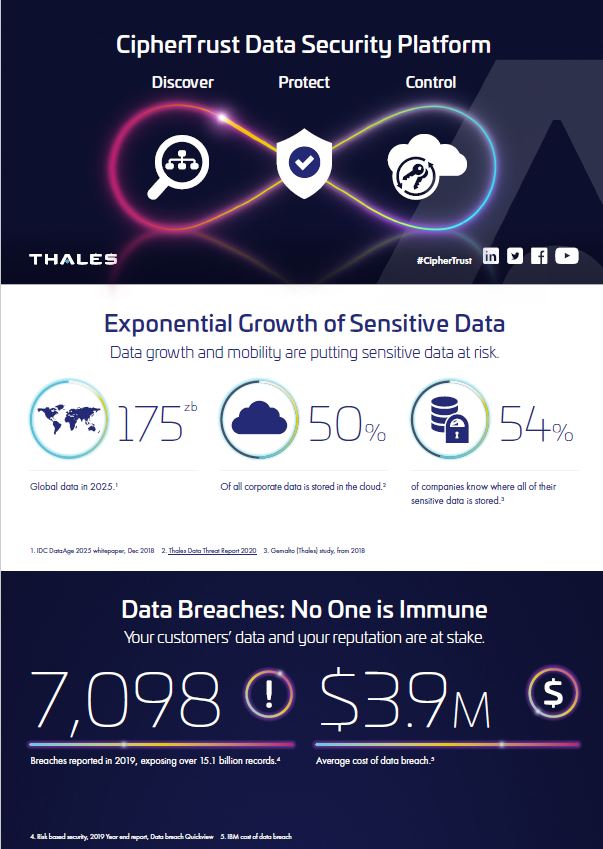
- Discover: An organization must be able to discover data wherever it resides and classify it. This data can be in many forms: files, databases, and big data and it can rest across storage on premises, in clouds, and across back-ups. Data security and compliance starts with finding exposed sensitive data before hackers and auditors. The CipherTrust Data Security Platform enables organizations to get complete visibility into sensitive data on-premises and in the cloud with efficient data discovery, classification, and risk analysis.
- Protect: Once an organization knows where its sensitive data is, protective measures such as encryption or tokenization can be applied. For encryption and tokenization to successfully secure sensitive data, the cryptographic keys themselves must be secured, managed and controlled by the organization. The CipherTrust Data Security Platform provides comprehensive data security capabilities, including file-level encryption with access controls, application-layer encryption, database encryption, static data masking, vaultless tokenization with policy-based dynamic data masking and vaulted tokenization to support a wide range of data protection use cases.
- Control: Finally, the organization needs to control access to its data and centralize key management. Every data security regulation and mandate requires organizations to be able to monitor, detect, control and report on authorized and unauthorized access to data and encryption keys. The CipherTrust Data Security Platform delivers robust enterprise key management across multiple cloud service providers (CSP) and hybrid cloud environments to centrally manage encryption keys and configure security policies so organizations can control and protect sensitive data in the cloud, on-premise and across hybrid environments.
Benefits
Simplify Data Security
Discover, protect, and control your organization’s most sensitive data on-premises and in the cloud on an integrated data security platform.
Accelerate Time to Compliance
Comprehensive data security capabilities, including data discovery and classification, encryption, granular access controls, audit logs, tokenization, and key management support ubiquitous data security and privacy requirements.
Secure Cloud Migration
Confidently move workloads to the cloud and hosted environments, and repatriate data back on-premises, knowing that your data remains in your control.
CipherTrust Data Security Platform
CipherTrust Manager
Key Management and Policies

CipherTrust Connectors

CipherTrust Enterprise Key Management
Centrally manage and store keys and policies for 3rd party devices
Resources
| Image | Title | Summary | Link |
|---|---|---|---|
| Solution Brief: Top 10 Reasons to Migrate to the CipherTrust Data Security Platform For Vormetric Customers | You relied on the Vormetric DSM platform over many years to provide centralized key management … | ||
| Solution Brief: Top 10 Reasons to Migrate to the CipherTrust Data Security Platform For KeySecure Customers | You relied on the KeySecure platform over many years to provide centralized key management and … | ||
| White Paper: Understanding Data Security for SAP | SAP provides the operational lifeblood of many enterprises with SAP modules providing essential functions that … | ||
| White Paper: Protecting sensitive data in and around SAP HANA | On the surface, encrypting the database instance using SAP native encryption would appear to be … | ||
| CipherTrust Data Security Platform Product Brief | Learn more about CipherTrust Data Security … | ||
| CTO Sessions Webcast On Demand: Top 10 Reasons to Protect Your Agency with CipherTrust Data Security Platform | In this installment of Thales TCT’s CTO Sessions Webcast Series, our Deputy CTO shared the … | ||
| CTO Sessions On Demand: Protecting Your Data in Their Cloud | Cloud Service Providers (CSPs) emphasize the shared responsibility model for securing data in the cloud … | ||
| CipherTrust Cloud Key Management Solutions for Amazon Web Services Solution Brief | Learn More About CipherTrust Cloud Key Management Solutions for Amazon Web … | ||
| Multi-Factor Authentication for CipherTrust Transparent Encryption | Learn more about Multi-Factor Authentication for CipherTrust Transparent … | ||
| CipherTrust Transparent Encryption for Teradata Vantage Solution Brief | Learn More About CipherTrust Transparent Encryption for Teradata … | ||
| CipherTrust Data Security Platform Self Guided Tour | … | ||
| On Demand Webinar: The Key Pillars for Protecting Sensitive Data | During this webinar, attendees learned how to develop a three-point strategy for protecting sensitive data … | ||
| On Demand Webinar: Fireside Chat: Data Protection for Multi-Domain Operations | The U.S. Military generates data at unprecedented rates, all the time, and in various locations … | ||
| On Demand Webinar: Complementing Splunk: Balancing Big Data Benefits & Big Risks | Federal agencies require a simple way to correlate all security-relevant data so they can manage … | ||
| CTO Sessions On Demand: Securing the Convergence of HPC and AI in the Enterprise | High-performance computing (HPC) has long expanded from research labs to commercial use. Computational modeling and … | ||
| Top 10 Reasons for Protecting Your Organization with CipherTrust Data Security Platform | Top 10 Reasons for Protecting Your Organization with CipherTrust Data Security … | ||
| Top 10 Reasons CipherTrust Intelligent Protection will Protect Your Data & Reduce Your Risk | Top 10 Reasons CipherTrust Intelligent Protection will Protect Your Data & Reduce Your … | ||
| White Paper: The Importance of KMIP Standard for Centralized Key Management | Today, protecting sensitive data is a fundamental requirement in virtually every business. What’s also nearly … | ||
| White Paper: The Case for Centralized Multicloud Encryption Key Management | Cloud consumers face a choice: using the cloud service provider’s (CSP) encryption or bringing their … | ||
| White Paper: The Key Pillars for Protecting Sensitive Data in Any Organization | This white paper outlines the challenges of data security in this age of data proliferation. … | ||
| White Paper: Key Management | This white paper looks back at the evolution of encryption and key management systems, and … | ||
| Protecting Data with Thales Key Management and Dell VxRail HCI System | Learn how to protect Data with Thales Key Management and Dell VxRail HCI … | ||
| Protecting Data with Thales CipherTrust Manager and Dell PowerEdge Server | Learn how to protect data with Thales CipherTrust Manager and Dell PowerEdge … | ||
| CipherTrust Teradata Protection Solution Brief | Learn more about CipherTrust Teradata … | ||
| White Paper: Own and Manage Your Encryption Keys | For agency leaders and IT administrators responsible for data security—from the most basic statistics to … | ||
| White Paper: NIST 800-53 Mapping to CipherTrust Data Security Platform | Thales TCT is a key partner in helping organizations to meet the standard. Focusing on … | ||
| Enterprise Key Management Solutions for KMIP Clients, TDE and LUKS Solution Brief | Learn More About Enterprise Key Management Solutions for KMIP Clients, TDE and … | ||
| Data Discovery & Classification Solution Brief | Learn more about Data Discovery & … | ||
| Data Discovery & Classification Product Brief | Learn more about Data Discovery & … | ||
| CipherTrust Transparent Encryption for Kubernetes Product Brief | Learn more about CipherTrust Transparent Encryption for … | ||
| Virtual CipherTrust Manager Product Brief | Learn more about Virtual CipherTrust … | ||
| White Paper: CipherTrust Transparent Encryption | CipherTrust Transparent Encryption enables quick, effective and transparent protection of data at the system level … | ||
| CipherTrust Transparent Encryption Product Brief | Learn more about CipherTrust Transparent … | ||
| CipherTrust Security Intelligence Product Brief | Learn more about CipherTrust Security … | ||
| CipherTrust Manager Product Brief | Learn more about CipherTrust … | ||
| CipherTrust Manager k570 Product Brief | Learn more about CipherTrust Manager … | ||
| CipherTrust Manager k160 Product Brief | Learn more about CipherTrust Manager … | ||
| CipherTrust Live Data Transformation Product Brief | Learn more about CipherTrust Live Data … | ||
| VMware and Thales TCT Integration Brief | VMware and Thales Deliver Secure Virtual Machine Encryption … | ||
| Integrated Data Discovery and Classification with Enhanced Protection Product Brief | Learn more about Integrated Data Discovery and Classification with Enhanced … | ||
| CipherTrust Encryption key management solutions for Microsoft® SQL Server® and Oracle® Database Solution Brief | Learn more about Thales TCT’s integration Encryption key management solutions for Microsoft SQL Server and … | ||
| CipherTrust Data Security Platform Data Sheet | Learn more about CipherTrust Data Security … | ||
| CipherTrust Data Protection Gateway Product Brief | Learn more about CipherTrust Data Protection … | ||
| Infographic: CipherTrust Data Security Platform Infographic | Learn more about CipherTrust Data Security … | ||
| White Paper: CipherTrust Data Security Platform Architecture | The CipherTrust Data Security Platform from Thales integrates data discovery, classification, and industry-leading data protection … | ||
| CipherTrust Cloud Key Manager Product Brief | Learn more about CipherTrust Cloud Key … | ||
| White Paper: Best Practices for Secure Cloud Migration | This white paper is intended to aid readers in forming a cloud security strategy and … | ||
| White Paper: Best Practices for Cloud Data Protection and Key Management | This paper describes security best practices for protecting sensitive data in the public cloud and … | ||
| Advanced data protection for AWS S3 with CipherTrust Transparent Encryption Solution Brief | To fully secure data in an untrusted and multi-tenant cloud environment, organizations must secure sensitive … | ||
| Avoiding Amazon S3 Data Leaks with Scalable Encryption and Access Controls Solution Brief | To fully secure data in an untrusted and multi-tenant cloud environment, organizations must maintain complete … |