The Military Health System’s MHS Genesis electronic health record system manages and stores personal health information (PHI) for service members, vet...
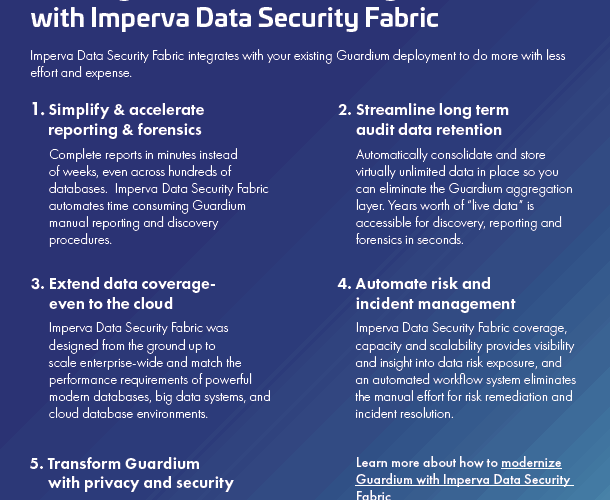
Read MoreDownload this infographic to learn how Imperva Data Security Fabric integrates with your existing Guardium deployment to do more with less effort and ...
Read MoreContemporary demands for data security and compliance have likely pushed your Guardium Database Activity Monitoring (DAM) program to its limits. Imper...
Read MoreOngoing government-wide zero trust implementations exemplify the fact that traditional end-point and perimeter-based security are not enough to protec...
Read MoreLearn more about Imperva Web Application Firewall Gateway.
Read MoreLearn about the essential capabilities of a Web Application Firewall and API Security Solution.
Read MoreLearn more about Imperva WAF Hardware Appliances.
Read MoreApplications have become mission-critical for organizations looking to drive rapid growth. They help facilitate an organization’s influence around the...
Read MoreBecause they are easily accessible and often serve as an entry point to valuable data, web applications are now—and always will be—a prime target for ...
Read MoreLearn more about Imperva Application Security.
Read More