Learn about Thales TCT’s solutions for Insider Risk Management.
Read MoreA Security Engineers Guide to Database Activity Monitoring Databases are key targets for hackers looking to steal data. However, there is insufficient...
Read MoreThe Military Health System’s MHS Genesis electronic health record system manages and stores personal health information (PHI) for service members, vet...
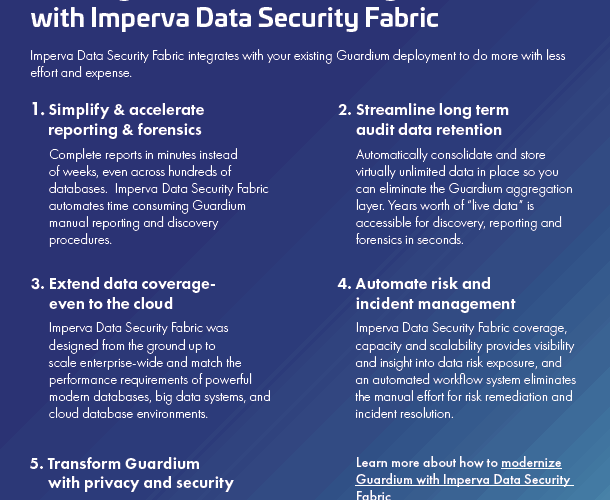
Read MoreDownload this infographic to learn how Imperva Data Security Fabric integrates with your existing Guardium deployment to do more with less effort and ...
Read MoreContemporary demands for data security and compliance have likely pushed your Guardium Database Activity Monitoring (DAM) program to its limits. Imper...
Read MoreOngoing government-wide zero trust implementations exemplify the fact that traditional end-point and perimeter-based security are not enough to protec...
Read MoreLearn how Imperva Data Security Fabric reduces Splunk operational costs and improves data-centric security insights.
Read MoreLearn how Imperva delivers a powerful pre-processor for Splunk optimizations and savings.
Read MoreLearn more about Imperva Data Security Fabric.
Read More