| Image | Title | Categories | Link | hf:doc_categories |
|---|---|---|---|---|
| Solution Brief: Hardware-Backed Zero Trust for Classified Data: Virtru Data Security Platform + Thales TCT Luna T-Series HSMs | ||||
| Video: A Roadmap for Securing AI Systems and Data | AI, Video | ai video | ||
| Solution Brief: Thales Retrieval Augmented Generative (RAG) AI Data Protection Solutions | AI | ai | ||
| Product Brief: Thales NFC Reader | Identity & Access Management | identity-access-management | ||
| CTO Sessions: Roadmap to Understanding Data Security Posture Management | Webcast | webcast | ||
| CTO Sessions On Demand: Trusted Data in Motion – Securing Government Communications in the PQC Era | HSE, Quantum, Webcast | hse quantum webcast | ||
| On Demand ATARC Webinar: Intersection of Quantum, AI, and Security | AI | ai | ||
| CTO Sessions On Demand: Zero Trust Best Practices for Federal Agencies | Zero Trust | zero-trust | ||
| eBook: Five Things to Consider when Choosing a DSPM Solution | CipherTrust | ciphertrust | ||
| Solution Brief: Data Security Posture Management | CipherTrust | ciphertrust | ||
| White Paper: Securing the Blind Spot: Unstructured Data Risk and Thales File Activity Monitoring | CipherTrust, White Paper | ciphertrust white-paper | ||
| Product Brief: CipherTrust Secrets Management | CipherTrust | ciphertrust | ||
| CTO Sessions On Demand: When AI Learns to Breach and Quantum Learns to Decrypt – The Endgame | AI, Quantum | ai quantum | ||
| Washington Technology Commentary: Why federal agencies must act now on post-quantum cryptography | Quantum | quantum | ||
| CTO Sessions Webcast On Demand: Intersection of Quantum, AI and Security | AI, Quantum, Webcast | ai quantum webcast | ||
| Solution Brief: Thales TCT Post-Quantum Cryptography Implementation | CipherTrust, HSM, Network Encryption, Quantum | ciphertrust hsm network-encryption quantum | ||
| Solution Brief: Insider Risk Management | Insider Risk Management | insider-risk-management | ||
| CTO Session Webcast On Demand: Intersection of AI and Security | AI, Webcast | ai webcast | ||
| Washington Technology Commentary: Why post-quantum security planning must start today | Quantum | quantum | ||
| GovLoop Blog Post: Quantum-Safe Encryption: What It Means, and Why Agencies Should Care | Quantum | quantum | ||
| On Demand GovLoop Webinar: Taking a Realistic Look at Quantum Computing in Government | Quantum, Webcast | quantum webcast | ||
| GovLoop Video: Quantum-Safe Encryption: Understanding the What, Why and How | Quantum | quantum | ||
| Govloop Video Interview: Quantum-Safe Encryption: What It Means, and Why Agencies Should Care | Quantum | quantum | ||
| CTO Sessions On Demand: Best Practices for Implementing Quantum-Resistant Security | Quantum | quantum | ||
| White Paper: Protect LLMs with CipherTrust Transparent Encryption | AI, CipherTrust, White Paper | ai ciphertrust white-paper | ||
| CTO Sessions On Demand: 2024 Data Threat Report – Federal Edition Webcast | ||||
| Solution Brief: Thales and Intel Collaborate to Enhance Trust in Confidential Computing By Enabling End-to-End Data Protection | CipherTrust | ciphertrust | ||
| Product Brief: IDBridge CT31 | Identity & Access Management | identity-access-management | ||
| Product Brief: Hades III USB Smart Card Reader | Identity & Access Management | identity-access-management | ||
| The Underappreciated Tactic of MITRE ATT&CK Framework – Collection | Imperva, Webcast | imperva webcast | ||
| Securing the Future: Navigation Post Quantum Cryptography Standards | Quantum, Webcast | quantum webcast | ||
| Solution Brief: Versasec Credential Management System | ||||
| CTO Sessions: Best Practices for Phishing-Resistant MFA: FIDO & PKI | Webcast | webcast | ||
| FedNewsNetwork Video Interview: Preparing for the intersection of AI, quantum computing | AI, Quantum | ai quantum | ||
| 2024 Thales Data Threat Report Federal Edition | ||||
| FedNewsNetwork Commentary: Preparing for the intersection of AI, quantum computing | AI, Quantum | ai quantum | ||
| CTO Sessions: Cloud HSM Best Practices | Cloud Security, HSM, Webcast | cloud-security hsm webcast | ||
| Blog Post: PQC Standards Released – Start Today | Quantum | quantum | ||
| Product Brief: IDPrime 3930 | Identity & Access Management | identity-access-management | ||
| Product Brief: IDPrime 940 and 940B | Identity & Access Management | identity-access-management | ||
| Product Brief: IDPrime 3940 | Identity & Access Management | identity-access-management | ||
| Solution Brief: Imperva Solutions for MHS Genesis | Imperva | imperva | ||
| CTO Sessions Webcast: Best Practices for Data in Transit Encryption | Network Encryption | network-encryption | ||
| Product Brief: SafeNet OTP 111 and SafeNet OTP 112 | Identity & Access Management | identity-access-management | ||
| Infographic: Five key benefits of enhancing IBM Guardium with Imperva Data Security Fabric | Imperva | imperva | ||
| Data Sheet: Modernize Guardium with Imperva Data Security Fabric | Imperva | imperva | ||
| Solution Brief: Securely Share CUI, SBU, and Secret Data with Coalition Partners with Thales TCT CipherTrust Data Security Platform | CipherTrust | ciphertrust | ||
| CTO Sessions Webcast: How-to Guide for Enhancing HPE Infrastructure Security | Webcast | webcast | ||
| Product Brief: Thales Fusion Authenticators | Identity & Access Management | identity-access-management | ||
| CTO Sessions Webcast: Thales TCT + Imperva Trusted End-to-End Data Security | Imperva, Webcast | imperva webcast | ||
| Product Brief: Luna T-Series Backup HSM | HSM | hsm | ||
| eBook: Thales TCT Solutions for CISA Zero Trust Maturity Model 2.0 | White Paper, Zero Trust | white-paper zero-trust | ||
| Solution Brief: Thales TCT Multi-Factor Authentication for CSfC for Mobile Access | CSfC | csfc | ||
| CTO Sessions: Quantum-Resistant Code Signing | HSM, Quantum, Webcast | hsm quantum webcast | ||
| CTO Sessions: Quantum Resistant Security | Webcast | webcast | ||
| Product Brief: IDCore 230/3230 | Identity & Access Management | identity-access-management | ||
| Product Brief: Imperva Web Application Firewall Gateway | Imperva | imperva | ||
| Solution Brief: WAAP Checklist | Imperva | imperva | ||
| Product Brief: Imperva WAF Hardware Appliances | Imperva | imperva | ||
| White Paper: WAAP Buyers Guide | Imperva, White Paper | imperva white-paper | ||
| White Paper: 10 Things Every Web Application Firewall Should Provide | Imperva | imperva | ||
| Product Brief: Imperva Application Security | Imperva | imperva | ||
| White Paper: Splunk Optimization by Imperva | Imperva | imperva | ||
| Solution Brief: Imperva for Splunk Optimizations | Imperva | imperva | ||
| Solution Brief: Data Risk Analytics Overview | Imperva | imperva | ||
| Solution Brief: Imperva Data Security Fabric Overview | Imperva | imperva | ||
| Product Brief: Imperva Data Security Fabric – Unstructured Data Discovery and Classification | Imperva | imperva | ||
| Product Brief: Imperva Data Risk Analytics | Imperva | imperva | ||
| Product Brief: Imperva Data Security Fabric | Imperva | imperva | ||
| Luna Tablet HSM Product Brief | HSM | hsm | ||
| Cipher Summit Resource Hub | Cipher Summit | cipher-summit | ||
| 2023 Thales Cloud Security Study | ||||
| Infographic: Top 6 Reasons for Choosing SafeNet eToken Fusion Series | Identity & Access Management | identity-access-management | ||
| Zero Trust: Top 5 Tips | Video, Zero Trust | video zero-trust | ||
| The Dual Faces of Quantum Computing: Opportunities and Threats in National Security | Quantum, Video | quantum video | ||
| CTO Sessions Webcast: Word on the Street – 2024’s Top Tech Trends | Webcast | webcast | ||
| White Paper: Quantum Resistant Code Signing Secured by Hardware Security Modules | HSM, Quantum, White Paper | hsm quantum white-paper | ||
| CTO Sessions On Demand Webcast: Everything You Need to Know About Phishing-Resistant MFA | Identity & Access Management, Webcast | identity-access-management webcast | ||
| White Paper: How to Choose a Secrets Management Solution | CipherTrust, White Paper | ciphertrust white-paper | ||
| White Paper: Meeting U.S. Government requirements for phishing-resistant MFA | Identity & Access Management | identity-access-management | ||
| eBook: The Comprehensive Guide on Phishing-Resistant MFA, Passkeys and FIDO security keys. | Identity & Access Management | identity-access-management | ||
| CTO Sessions Webcast: A Guide to BYOK and HYOK for AWS, Azure, Google, Oracle and More | Cloud Security, Webcast | cloud-security webcast | ||
| Solution Brief: CipherTrust Cloud Key Management for Oracle Cloud Infrastructure | CipherTrust | ciphertrust | ||
| Product Brief: Thales FIDO2 Devices | Identity & Access Management | identity-access-management | ||
| Product Brief: SafeNet Trusted Access | Identity & Access Management | identity-access-management | ||
| Product Brief: SafeNet IDPrime PIV | Identity & Access Management | identity-access-management | ||
| Product Brief: SafeNet OTP Display Card | Identity & Access Management | identity-access-management | ||
| Product Brief: SafeNet eToken 5300 Series | Identity & Access Management | identity-access-management | ||
| Product Brief: SafeNet eToken 5110 series | Identity & Access Management | identity-access-management | ||
| Solution Brief: Top 10 Reasons to Migrate to the CipherTrust Data Security Platform For Vormetric Customers | CipherTrust, Vormetric | ciphertrust vormetric | ||
| Solution Brief: Top 10 Reasons to Migrate to the CipherTrust Data Security Platform For KeySecure Customers | CipherTrust, KeySecure | ciphertrust keysecure | ||
| Infographic: Thales CV1000 Virtual Encryptor | Network Encryption | network-encryption | ||
| Video: Thales High Speed Encryptors Demo | Network Encryption, Video | network-encryption video | ||
| Video: Securing 5G Private Networks with Thales High Speed Encryptors | Network Encryption, Video | network-encryption video | ||
| Thales Security Solutions for Google Workspace | ||||
| CTO Sessions Webcast On Demand: AI & Cybersecurity | Votiro, Webcast | votiro webcast | ||
| White Paper: Understanding Data Security for SAP | CipherTrust, CipherTrust Integrations, White Paper | ciphertrust ciphertrust-integrations white-paper integrations | ||
| White Paper: Protecting sensitive data in and around SAP HANA | CipherTrust, CipherTrust Integrations, White Paper | ciphertrust ciphertrust-integrations white-paper integrations | ||
| Thales Secures SAP Data with Dell in Any-premises | CipherTrust, CipherTrust Integrations | ciphertrust ciphertrust-integrations integrations | ||
| Achieving Security and Compliance for SAP HANA with CipherTrust Transparent Encryption | CipherTrust, CipherTrust Integrations | ciphertrust ciphertrust-integrations integrations | ||
| CipherTrust Tokenization for SAP ERP Solutions | CipherTrust, CipherTrust Integrations | ciphertrust ciphertrust-integrations integrations | ||
| CipherTrust Cloud Key Manager for SAP Applications | CipherTrust, CipherTrust Integrations | ciphertrust ciphertrust-integrations integrations | ||
| CTO Sessions Webcast On Demand: Network Encryption Boot Camp – A Guide to Network Encryption from the Core to the Cloud to the Edge | Network Encryption, Webcast | network-encryption webcast | ||
| CTO Sessions Webcast On Demand: HSM Boot Camp – A Guide to HSM Deployments from the Core to the Cloud to the Edge | HSM, Webcast | hsm webcast | ||
| CipherTrust Data Security Platform Product Brief | CipherTrust | ciphertrust | ||
| CTO Sessions Webcast On Demand: Deliver Secure Hyper-Converged Infrastructure Solutions | CipherTrust, Webcast | ciphertrust webcast | ||
| Dell PowerProtect Cyber Recovery and Thales CipherTrust Manager | CipherTrust, CipherTrust Integrations | ciphertrust ciphertrust-integrations integrations | ||
| Secure Edge Data with Multi-Layer Encryption through HPE Edgeline and Thales TCT CipherTrust k160 | CipherTrust, CipherTrust Integrations, Integrations | ciphertrust ciphertrust-integrations integrations | ||
| HPE GreenLake and Thales TCT CipherTrust Data Security Platform | CipherTrust, CipherTrust Integrations, Integrations | ciphertrust ciphertrust-integrations integrations | ||
| Solution Brief: Quantum Resistant High Speed Network Encryption | CSfC, Network Encryption | csfc network-encryption | ||
| Solution Brief: Thales TCT CSfC Capabilities | CSfC | csfc | ||
| CipherTrust Transparent Encryption Ransomware Protection | CipherTrust | ciphertrust | ||
| CTO Sessions Webcast On Demand: Zero Trust – Beyond the Buzzword | Webcast, Zero Trust | webcast zero-trust | ||
| FCW/NetGov’s Zero Trust Workshop Replay: Zero Trust: Buzzword to Brass Tacks | Video, Zero Trust | video zero-trust | ||
| CTO Sessions Webcast On Demand: Building a Root of Trust in How to Secure the Most Sensitive Data | HSM, Webcast | hsm webcast | ||
| CTO Sessions Webcast On Demand: Top 10 Reasons to Protect Your Agency with CipherTrust Data Security Platform | CipherTrust, Webcast | ciphertrust webcast | ||
| Votiro | Secure File Gateway Partners | secure-file-gateway-partners | ||
| CTO Sessions Webcast On Demand: Taking Control of 2023’s Top Tech Trends | Cloud Security, Edge Solutions, Network Encryption, Quantum, Webcast, Zero Trust | cloud-security edge-solutions network-encryption quantum webcast zero-trust | ||
| CTO Sessions On Demand: Protecting Your Data in Their Cloud | CipherTrust, Cloud Security, Webcast | ciphertrust cloud-security webcast | ||
| CTO Sessions On Demand: Are You Quantum Ready? | Quantum, Webcast | quantum webcast | ||
| CipherTrust Cloud Key Management Solutions for Amazon Web Services Solution Brief | CipherTrust, CipherTrust Integrations, Cloud Security | ciphertrust ciphertrust-integrations cloud-security integrations | ||
| Multi-Factor Authentication for CipherTrust Transparent Encryption | CipherTrust | ciphertrust | ||
| Luna as a Service Solution Brief | Cloud Security, HSM, Luna as a Service, Luna Credential System | cloud-security hsm luna-as-a-service luna-credential-system | ||
| CTO Sessions On Demand: Data Protection at the Edge | Edge Solutions, Webcast | edge-solutions webcast | ||
| CipherTrust Transparent Encryption for Teradata Vantage Solution Brief | CipherTrust Integrations, Integrations | ciphertrust-integrations integrations | ||
| ISC and Thales TCT HSM Solution Brief | HSM Integrations, Integrations | hsm-integrations integrations | ||
| Securing Infoblox DNSSEC Implementations with Thales TCT’s Luna Network HSM Solution Brief | HSM Integrations, Integrations | hsm-integrations integrations | ||
| HID ActiveID and Thales TCT Luna Network HSM Solution Brief | HSM Integrations, Integrations | hsm-integrations integrations | ||
| CTERA Enterprise File Services Platform and Thales TCT CipherTrust Manager Solution Brief | CipherTrust Integrations, Integrations | ciphertrust-integrations integrations | ||
| Cohesity | ||||
| Thales TCT: Protecting the Most Vital Data from the Core to the Cloud to the Field | Video | video | ||
| Luna Credential System Video | Luna Credential System, Video | luna-credential-system video | ||
| Luna Credential System & UiPath RPA: Addressing Federal CAC/PIV Requirements with PKI Authentication | Luna Credential System, Video | luna-credential-system video | ||
| How to Integrate UiPath with Thales TCT’s Luna Credential System | LCS Integrations, Luna Credential System, Video | lcs-integrations luna-credential-system video integrations | ||
| Product Demo: Protecting AWS S3 Buckets: AWS KMS vs Transparent Encryption COS S3 from Thales | Cloud Security, Video | cloud-security video | ||
| Thales IDPrime FIDO 2.0 Smartcard Demo | Identity & Access Management, Video | identity-access-management video | ||
| CipherTrust Data Security Platform Self Guided Tour | CipherTrust, Video | ciphertrust video | ||
| Introduction to Thales’ CipherTrust Enterprise Key Management Solutions | CipherTrust | ciphertrust | ||
| CipherTrust Data Discovery and Classification Walkthrough | Video | video | ||
| Video: CipherTrust Data Discovery & Classification | Video | video | ||
| Cyber EO Compliance Video Series – Part 2 – Multi-Factor Authentication | Compliance, Video | compliance video | ||
| Top 5 Ways to Comply with the White House EO on Cybersecurity – Part 1 – Setting the Stage | Compliance, Video | compliance video | ||
| Cyber EO Compliance Video Series – Part 3 – Data at Rest Encryption | Compliance, Webcast | compliance webcast | ||
| Cyber EO Compliance Video Series – Part 4 – Data in Transit Encryption | Compliance, Video | compliance video | ||
| Cyber EO Compliance Video Series – Part 5 – Securing Cloud Deployments | Compliance, Video | compliance video | ||
| Cyber EO Compliance Video Series – Part 6 – Implementing a Zero Trust Architecture | Compliance, Video | compliance video | ||
| On Demand Webinar: Rapid Protection for Teradata Database and Big Data Environments | CipherTrust, Webcast | ciphertrust webcast | ||
| On Demand Webinar: No-Excuse Defenses Against Supply Chain Attacks | Votiro, Webcast | votiro webcast | ||
| On Demand Webinar: Best Practices for Data Visibility | CipherTrust, Webcast | ciphertrust webcast | ||
| On Demand Webinar: Best Practices for Cloud Data Protection | Cloud Security, Webcast | cloud-security webcast | ||
| On Demand Webinar – Intelligence Community: Cyber Security is National Security | Cloud Security, Webcast, Zero Trust | cloud-security webcast zero-trust | ||
| On Demand Webinar: The Key Pillars for Protecting Sensitive Data | CipherTrust, Webcast | ciphertrust webcast | ||
| On Demand Webinar: Fireside Chat: Data Protection for Multi-Domain Operations | CipherTrust, Webcast | ciphertrust webcast | ||
| On Demand Webinar: Shifting the Mindset from “Breach Prevention” to “Acceptance” | Webcast, Zero Trust | webcast zero-trust | ||
| On Demand Webinar: Building a Root of Trust to Secure the Most Sensitive Data | HSM, Webcast | hsm webcast | ||
| On Demand Webinar: Complementing Splunk: Balancing Big Data Benefits & Big Risks | CipherTrust, CipherTrust Integrations, Webcast | ciphertrust ciphertrust-integrations webcast integrations | ||
| On Demand Webinar: How To Issue Hardware-Based Identity Credentials To Software Robots | Luna Credential System, RPA, Webcast | luna-credential-system rpa webcast | ||
| On Demand Master Class: Zero Trust Beyond the Buzzword | Webcast, Zero Trust | webcast zero-trust | ||
| CTO Sessions On Demand: Securing the Convergence of HPC and AI in the Enterprise | CipherTrust, CipherTrust Integrations, Webcast | ciphertrust ciphertrust-integrations webcast integrations | ||
| CTO Sessions On Demand: Best Practices for Data in Transit Encryption | Network Encryption, Webcast | network-encryption webcast | ||
| CTO Sessions On Demand: Preventing Ransomware in Microsoft 365 Environments | Votiro, Webcast | votiro webcast | ||
| CipherTrust Platform Community Edition | CipherTrust | ciphertrust | ||
| Top 10 Reasons for Protecting Your Organization with CipherTrust Data Security Platform | CipherTrust | ciphertrust | ||
| Top 10 Reasons CipherTrust Intelligent Protection will Protect Your Data & Reduce Your Risk | CipherTrust | ciphertrust | ||
| White Paper: The Importance of KMIP Standard for Centralized Key Management | CipherTrust, White Paper | ciphertrust white-paper | ||
| White Paper: The Case for Centralized Multicloud Encryption Key Management | CipherTrust, Cloud Security, White Paper | ciphertrust cloud-security white-paper | ||
| White Paper: The Key Pillars for Protecting Sensitive Data in Any Organization | CipherTrust, White Paper | ciphertrust white-paper | ||
| Solution Brief: Thales TCT Zero Trust Solutions | Zero Trust | zero-trust | ||
| White Paper: Securing the Keys to the Kingdom with Splunk and Thales | CipherTrust, CipherTrust Integrations, Integrations, White Paper | ciphertrust ciphertrust-integrations integrations white-paper | ||
| Thales TCT and Splunk Solution Brief | CipherTrust, CipherTrust Integrations, Integrations | ciphertrust ciphertrust-integrations integrations | ||
| Thales TCT Solutions for the NSM on Improving Cybersecurity of NSS Solution Brief | Compliance | compliance | ||
| Microsoft Azure Advanced Data Protection Solution Brief | CipherTrust Integrations, Cloud Security, Integrations | ciphertrust-integrations cloud-security integrations | ||
| Thales TCT Solutions for White House Executive Order on Cybersecurity | Compliance | compliance | ||
| Thales Trusted Cyber Technologies Solutions for Continuous Diagnostics and Mitigation DEFEND | Compliance | compliance | ||
| Thales Trusted Cyber Technologies Product Overview | ||||
| White Paper: Key Management | CipherTrust, White Paper | ciphertrust white-paper | ||
| Panasas PanFS and Thales TCT CipherTrust Manager Solution Brief | CipherTrust Integrations, Integrations | ciphertrust-integrations integrations | ||
| Thales TCT Luna Hardware Security Solutions for Microsoft Certificate Services | HSM Integrations, Integrations | hsm-integrations integrations | ||
| Quantum Enhanced Keys Solution Brief | HSM, Quantum | hsm quantum | ||
| Data Protection Solutions for the Edge Solution Brief | Edge Solutions | edge-solutions | ||
| Protecting Data with Thales Key Management and Dell VxRail HCI System | CipherTrust Integrations, Integrations | ciphertrust-integrations integrations | ||
| Protecting Data with Thales CipherTrust Manager and Dell PowerEdge Server | CipherTrust, CipherTrust Integrations, Integrations | ciphertrust ciphertrust-integrations integrations | ||
| Solution Brief: Thales TCT Luna HSMs for Commercial Solutions for Classified (CSfC) | Compliance, CSfC, HSM | compliance csfc hsm | ||
| White Paper: NIST Cybersecurity Framework and Ransomware Prevention Guidance Mapping | Compliance | compliance | ||
| CipherTrust Teradata Protection Solution Brief | CipherTrust, CipherTrust Integrations | ciphertrust ciphertrust-integrations integrations | ||
| White Paper: Thales TCT Solutions for CMMC | Compliance | compliance | ||
| Thales Authentication Family Brief | Identity & Access Management | identity-access-management | ||
| UiPath RPA Cryptographic Authentication with Luna Credential System | LCS Integrations, Luna Credential System | lcs-integrations luna-credential-system integrations | ||
| Securing UiPath Credential Stores with Luna Vault Solution Brief | LCS Integrations, Luna Credential System | lcs-integrations luna-credential-system integrations | ||
| Votiro Secure File Gateway vs Secure Email Gateway Solution Brief | Votiro | votiro | ||
| Votiro Secure File Gateway for Web Applications | Votiro | votiro | ||
| Votiro Secure File Gateway for Email | Votiro | votiro | ||
| Votiro + Office 365 Solution Brief | Votiro | votiro | ||
| VMware and Thales Deliver Secure Hyper-Converged Infrastructure Solution Brief | CipherTrust, CipherTrust Integrations, Integrations | ciphertrust ciphertrust-integrations integrations | ||
| VMware and Thales Deliver Secure Virtual Machine Encryption Solution Brief | CipherTrust, CipherTrust Integrations, Integrations | ciphertrust ciphertrust-integrations integrations | ||
| Vormetric Data Security Platform Product Brief | Vormetric | vormetric | ||
| SureDrop Product Brief | SureDrop | suredrop | ||
| Industry Insight: Supply Chain Risk Management | White Paper | white-paper | ||
| DoD STIG Compliance Virtualization-Based Security – External Key Management Solution Brief | CipherTrust, Compliance | ciphertrust compliance | ||
| White Paper: Splunk and Thales Industry Standard Protection for Your Log Data | CipherTrust, CipherTrust Integrations, Integrations, White Paper | ciphertrust ciphertrust-integrations integrations white-paper | ||
| Security Management Center Product Brief | Network Encryption | network-encryption | ||
| Research Study: Security Weaknesses in Data in Motion Identified in Cybersecurity Survey | Network Encryption, White Paper | network-encryption white-paper | ||
| White Paper: Securing SD-WAN | Network Encryption, White Paper | network-encryption white-paper | ||
| White Paper: Securing Network-Attached HSMs | HSM, White Paper | hsm white-paper | ||
| Product Brief: SafeNet Authentication Service Private Cloud Edition | Identity & Access Management | identity-access-management | ||
| Smart Card 650 Product Brief | Identity & Access Management | identity-access-management | ||
| eBook: Ryuk: Everything You Need to Know About the Ransomware Targeting U.S. Governments & Government Agencies | Votiro | votiro | ||
| Robotic Process Automation Industry Insight | Luna Credential System, RPA | luna-credential-system rpa | ||
| White Paper: Roots of Trust | HSM, White Paper | hsm white-paper | ||
| Redhat and Thales TCT Solution Brief | HSM Integrations, Integrations | hsm-integrations integrations | ||
| White Paper: Prevent Ransomware Attacks from Disrupting Your Agency with the CipherTrust Platform | White Paper | white-paper | ||
| White Paper: Own and Manage Your Encryption Keys | CipherTrust, White Paper | ciphertrust white-paper | ||
| Nutanix and Thales TCT Solution Brief | CipherTrust, CipherTrust Integrations, Integrations | ciphertrust ciphertrust-integrations integrations | ||
| White Paper: NIST 800-57 Recommendations for Key Management Requirements Analysis | Compliance, White Paper | compliance white-paper | ||
| White Paper: NIST 800-53 Mapping to CipherTrust Data Security Platform | CipherTrust, White Paper | ciphertrust white-paper | ||
| White Paper: Network Independent Encryption | Network Encryption, White Paper | network-encryption white-paper | ||
| Network Encryption Family Overview Brief | Network Encryption | network-encryption | ||
| NetApp and Thales TCT Solution Brief | CipherTrust, CipherTrust Integrations, Integrations | ciphertrust ciphertrust-integrations integrations | ||
| Solution Brief: Best Security Practices for milCloud Data Migration | Cloud Security | cloud-security | ||
| White Paper: Malicious Macros | Votiro, White Paper | votiro white-paper | ||
| White Paper: MACsec for WAN and High Assurance Encryptors | Network Encryption, White Paper | network-encryption white-paper | ||
| Luna PCIe HSM Product Brief | HSM | hsm | ||
| Luna Network HSM Product Brief | HSM | hsm | ||
| Luna G5 for Government HSM Product Brief | HSM | hsm | ||
| Luna Credential System Product Brief | Luna Credential System | luna-credential-system | ||
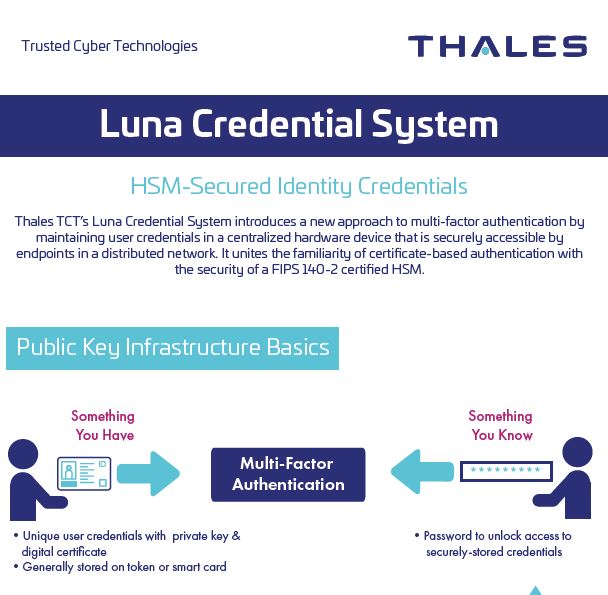
| Infographic: Luna Credential System | Luna Credential System | luna-credential-system | ||
| KeySecure G160 Product Brief | KeySecure | keysecure | ||
| SafeNet IDPrime PIV | Identity & Access Management | identity-access-management | ||
| Product Brief: SafeNet IDPrime 930/931 Series | Identity & Access Management | identity-access-management | ||
| Thales High Speed Encryption Solutions Family Overview | Network Encryption | network-encryption | ||
| White Paper: High Speed Encryption Solutions Across MPLS Networks | Network Encryption, White Paper | network-encryption white-paper | ||
| Thales TCT HSM Product Family Overview Brief | HSM | hsm | ||
| eBook: High Speed Ethernet WAN | Network Encryption, White Paper | network-encryption white-paper | ||
| HPE servers and storage with Thales CipherTrust Data Security Platform Solution Brief | CipherTrust, CipherTrust Integrations, Integrations | ciphertrust ciphertrust-integrations integrations | ||
| HPE 3PAR StoreServ and Thales CipherTrust Manager | CipherTrust, CipherTrust Integrations, Integrations | ciphertrust ciphertrust-integrations integrations | ||
| How Ransomware attacks leverage unprotected RDPs Solution Brief | Identity & Access Management | identity-access-management | ||
| White Paper: HIPAA Compliance Checklist | Compliance | compliance | ||
| White Paper: High Assurance Encryption for Healthcare Network Data | Compliance, White Paper | compliance white-paper | ||
| White Paper: Ethernet WAN Solutions Compared | Network Encryption, White Paper | network-encryption white-paper | ||
| Entrust and Thales TCT HSMs Solution Brief | ||||
| Enterprise Key Management Solutions for KMIP Clients, TDE and LUKS Solution Brief | CipherTrust | ciphertrust | ||
| Enterprise Key Management for NetApp Solution Brief | CipherTrust, CipherTrust Integrations, Integrations | ciphertrust ciphertrust-integrations integrations | ||
| eBook: Encrypt Everything | White Paper | white-paper | ||
| White Paper: Data Protection at the Edge | Edge Solutions, White Paper | edge-solutions white-paper | ||
| Data Discovery & Classification Solution Brief | CipherTrust | ciphertrust | ||
| Data Discovery & Classification Product Brief | CipherTrust | ciphertrust | ||
| White Paper: Top Five Ways to Address Requirements in National Security Memo on Improving Cybersecurity of National Security Systems | Compliance, White Paper | compliance white-paper | ||
| CV1000 Product Brief | Network Encryption | network-encryption | ||
| CipherTrust Transparent Encryption for Kubernetes Product Brief | CipherTrust | ciphertrust | ||
| CN9120 Product Brief | Network Encryption | network-encryption | ||
| CN6140 Product Brief | Network Encryption | network-encryption | ||
| CN6100 Product Brief | Network Encryption | network-encryption | ||
| CN6010 Product Brief | Network Encryption | network-encryption | ||
| CN4020 Product Brief | Network Encryption | network-encryption | ||
| CN4010 Product Brief | Network Encryption | network-encryption | ||
| CM7 Network Manager Product Brief | Network Encryption | network-encryption | ||
| White Paper: CJIS Data-in-Transit Encryption Standards | Compliance, Network Encryption | compliance network-encryption | ||
| Virtual CipherTrust Manager Product Brief | CipherTrust | ciphertrust | ||
| White Paper: CipherTrust Transparent Encryption | CipherTrust | ciphertrust | ||
| CipherTrust Transparent Encryption Product Brief | CipherTrust | ciphertrust | ||
| CipherTrust Security Intelligence Product Brief | CipherTrust | ciphertrust | ||
| CipherTrust Manager Product Brief | CipherTrust | ciphertrust | ||
| CipherTrust Manager k570 Product Brief | CipherTrust | ciphertrust | ||
| CipherTrust Manager k160 Product Brief | CipherTrust | ciphertrust | ||
| CipherTrust Live Data Transformation Product Brief | CipherTrust | ciphertrust | ||
| VMware and Thales TCT Integration Brief | CipherTrust | ciphertrust | ||
| Thales TCT CipherTrust Enterprise Key Management and Dell Technologies | CipherTrust, CipherTrust Integrations | ciphertrust ciphertrust-integrations integrations | ||
| Integrated Data Discovery and Classification with Enhanced Protection Product Brief | CipherTrust | ciphertrust | ||
| CipherTrust Encryption key management solutions for Microsoft® SQL Server® and Oracle® Database Solution Brief | CipherTrust | ciphertrust | ||
| CipherTrust Data Security Platform Data Sheet | CipherTrust | ciphertrust | ||
| CipherTrust Data Protection Gateway Product Brief | CipherTrust | ciphertrust | ||
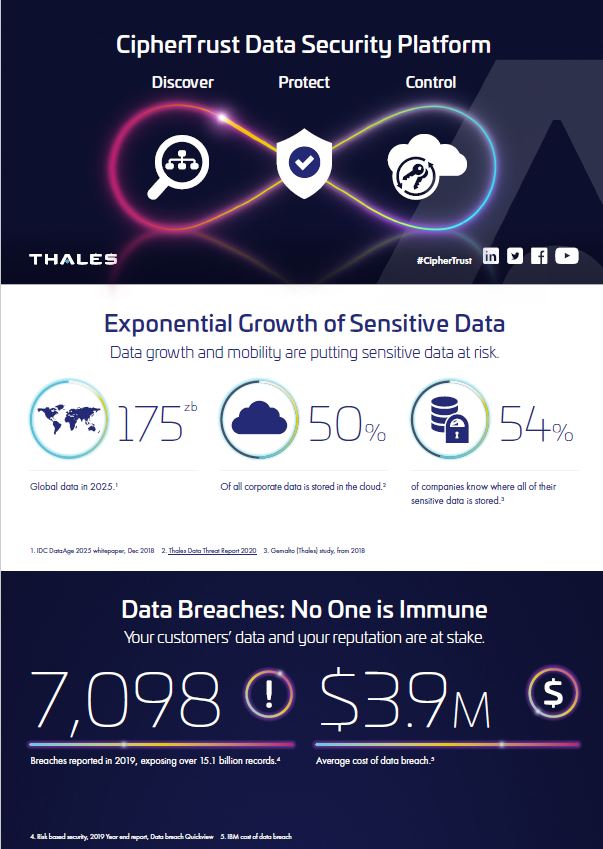
| Infographic: CipherTrust Data Security Platform Infographic | CipherTrust | ciphertrust | ||
| White Paper: CipherTrust Data Security Platform Architecture | CipherTrust | ciphertrust | ||
| White Paper: Continuous Diagnostics and Mitigation: Data Protection & Assurance | Compliance | compliance | ||
| CipherTrust Cloud Key Management Product Brief | CipherTrust, Cloud Security | ciphertrust cloud-security | ||
| RPA Cryptographic Authentication — Thales TCT and Blue Prism | LCS Integrations, Luna Credential System, RPA | lcs-integrations luna-credential-system rpa integrations | ||
| White Paper: Best Practices for Securing Network Function Virtualization Environment | Network Encryption | network-encryption | ||
| White Paper: Best Practices for Implementing the White House Executive Order on Improving the Nation’s Cybersecurity Infrastructure | Compliance, Identity & Access Management | compliance identity-access-management | ||
| White Paper: Best Practices for Cryptographic Key Management | HSM, White Paper | hsm white-paper | ||
| White Paper: Best Practices for Secure Cloud Migration | Cloud Security | cloud-security | ||
| White Paper: Best Practices for Cloud Data Protection and Key Management | Cloud Security | cloud-security | ||
| Advanced data protection for AWS S3 with CipherTrust Transparent Encryption Solution Brief | CipherTrust Integrations, Cloud Security, Integrations | ciphertrust-integrations cloud-security integrations | ||
| Avoiding Amazon S3 Data Leaks with Scalable Encryption and Access Controls Solution Brief | CipherTrust Integrations, Cloud Security, Integrations | ciphertrust-integrations cloud-security integrations | ||
| AppViewX and Thales Trusted Cyber Technologies Luna Network HSM Solution Brief | ||||
| White Paper: Secure Multicast Transmission | Network Encryption, White Paper | network-encryption white-paper | ||
| Solution Brief: Votiro + Office 365 | ||||
| Solution Brief: Data Protection Solutions for the Edge |